Greetings,
I’m excited to walk you through a recent accomplishment – a Networking Engineering project that included establishing a network infrastructure based on detailed specifications. Let’s get to the heart of this project, understanding the aims, implementation, and results.
Project Overview: Building a Robust Network Infrastructure Our scope was to build a robust network architecture aligning with specific criteria. We embarked on this journey to implement the complete environment.
Company Details and Network Requirements: We began by outlining the network’s fundamental requirements:
- Number of Users: ~250
- Number of Devices: ~300
- Number of Departments: ~10
- Network Requirements: High Availability, Security, and Connectivity to the Internet.
Implementation Journey: Our implementation journey was marked by meticulous steps:
- VLAN / IP Addressing: Using a VLSM Addressing Scheme, we divided the network according to the device count in each department. A separate VLAN and Subnet were established for management purposes.
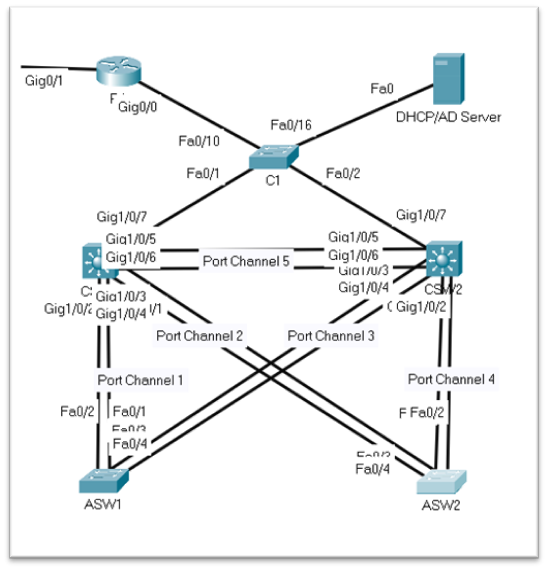
- Network Design: We leveraged two Multilayer Switches, three Access Layer Switches, one Router, and a Server to craft the network design. High Availability was ensured through EtherChannel and HSRP configuration. Inter-VLAN routing was enabled using Layer 3 Switches.
- Services Implementation: Our network implementation wouldn’t be complete without integrating vital protocols and software to fulfill the specified requirements. Let’s dive into the detailed implementation of each component that contributed to the network’s robustness and functionality.
- High Availability:
- EtherChannel: We implemented EtherChannel, a port aggregation technology, to bundle multiple physical ports into a single logical port between the Layer 3 switches and the Access Layer Switches. This not only increased available bandwidth but also enhanced redundancy and load balancing.
- HSRP (Hot Standby Router Protocol): Using HSRP, we ensured seamless failover by designating one of the Layer 3 switches as the active router and the other as standby. The active router managed traffic while the standby router took over in case of failure.
- Security (Authentication):
- Active Directory Server: We set up an Active Directory (AD) Server, a centralized authentication and authorization service. It enabled efficient management of users, groups, and computers within the network.
- Password Encryption: By encrypting passwords, we bolstered security against unauthorized access.
- Privilege Configurations: Configured privileged EXEC passwords ensured controlled access to critical configurations within all the network devices.
- SSH Configuration: Secure Shell (SSH) replaced insecure Telnet for remote management, enhancing security during command-line interactions.
- Access Control Lists (VACLs): Implemented at the Layer 3 level, these allowed us to control traffic between VLANs, strengthening network segmentation and security.
- Connectivity to the Internet:
- Router Configuration: Our router was configured to accept DHCP addresses from the external network, enabling it to connect to the internet dynamically.
- Network Address Translation (NAT) Overload: NAT Overload (or Port Address Translation, PAT) enabled multiple devices within our network to share a single public IP address, facilitating internet access.
- DHCP Server Setup: We implemented a DHCP Server to automatically assign IP addresses and network configuration information to devices within the network, with a separate DHCP pool for each of the devices within a VLAN.
- High Availability:
Each of these protocols and software components played a pivotal role in shaping the network’s performance, security, and accessibility. This comprehensive integration not only met the project’s requirements but also imparted invaluable practical insights into real-world networking scenarios.
Results and Insights: Navigating the Network Landscape
As we wrap up this journey through our Networking Engineering project, it’s essential to shed light on the results we achieved and the insights gained during this hands-on endeavor. Let’s delve into how our meticulous planning and implementation unfolded, and the valuable insights we gathered from the entire process.
Network Implementation and Results:
- CSW1 | CSW2: Our EtherChannel setup between Access Layer Switches and Core Layer Switches proved successful, delivering increased bandwidth and fault tolerance. HSRP functionality ensured smooth router failover.
- Router – R1: Our router efficiently received DHCP addresses from the external network, while NAT Overload enabled seamless internet access for internal devices.
- Server: Our Active Directory Server streamlined user and group management, while DHCP assignments provided dynamic IP allocation.
Network Insights:
- Redundancy Matters: Implementing EtherChannel and HSRP underscored the importance of redundancy in network design. These technologies ensured high availability and reduced downtime.
- Authentication’s Role: The Active Directory Server’s role in user authentication highlighted the significance of centralized user management for secure access.
- Security through Segmentation: VLANs and ACLs reinforced the principle of network segmentation, which enhances security by restricting traffic flow between different segments.
- NAT for Internet Access: NAT Overload emerged as a facilitator for allowing multiple devices to share a single public IP, a critical requirement for internet connectivity.
Practical Insights:
- Configuration Challenges: Hands-on configuration offered insights into the challenges of real-world network implementation, ranging from syntax accuracy to understanding protocol interactions.
- Holistic Network Design: Integrating protocols and services showed the interconnected nature of network components. A strong network depends on well-integrated components rather than separate configurations.
Professional Growth:
- Applied Knowledge: Our project translated theoretical knowledge into practical expertise. This hands-on experience is invaluable for professionals venturing into network administration.
- Critical Thinking: Troubleshooting and optimizing configurations honed our critical thinking skills, an essential asset in the dynamic world of IT.
In conclusion, our Networking Engineering project offered us a glimpse into the world of network administration, underlining the significance of well-rounded knowledge, meticulous planning, and hands-on experience. This project’s insights will undoubtedly serve as a foundation as we continue exploring the multifaceted realm of networking and technology.
Stay tuned for more insights and explorations on mustafacs.tech, where I’ll be sharing my journey and discoveries in the ever-evolving field of networking.