In the world of cybersecurity, staying ahead of malicious actors and understanding their tactics is paramount. Recently, an attack on MGM Resorts made headlines, showcasing how even large organizations are susceptible to cyber threats. In this blog post, I will apply the Unified Kill Chain (UKC) methodology, which I learned about in the TryHackMe “Unified Kill Chain” room, to dissect this high-profile incident. It’s important to note that this analysis is not exhaustive, as full details of the attack have not been released.
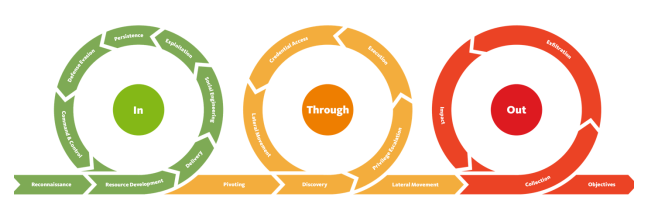
Understanding the Unified Kill Chain (UKC) Framework
When it comes to comprehending and combating cybersecurity threats, having a robust framework is essential. The Unified Kill Chain (UKC) is a modern and highly detailed framework that plays a pivotal role in understanding the intricacies of cyberattacks.
Benefits of the Unified Kill Chain (UKC) Framework:
- Modern: The UKC framework was released in 2017 and updated in 2022. This makes it more relevant in today’s rapidly evolving cybersecurity landscape. Some other frameworks, like MITRE’s, were released in 2013 when the landscape was different.
- Detailed: The UKC is incredibly detailed, comprising 18 phases. In contrast, many other frameworks have only a small handful of phases.
- Comprehensive: The UKC covers an entire attack lifecycle, including reconnaissance, exploitation, post-exploitation, and even identifying an attacker’s motivation. Many other frameworks cover a limited number of phases.
- Realistic: One unique aspect of the UKC is that it highlights a more realistic attack scenario. In practice, various stages often reoccur. For instance, after exploiting a machine, an attacker might revert to reconnaissance to pivot to another system. Other frameworks might not account for these iterative phases during an attack.
Now, let’s apply this framework to the MGM Resorts cyberattack.
The MGM Resorts Cyberattack:
MGM Resorts, a prominent casino chain with numerous properties worldwide, faced a cybersecurity incident that disrupted its operations. Here’s a breakdown of how the UKC framework can be applied to this situation:

1. Reconnaissance: The attack on MGM Resorts appears to have started with reconnaissance activities. The attackers, believed to be the Scattered Spider group, likely gathered information about the company, including employee details found on LinkedIn.
2. Resource Development: Unfortunately, the articles do not provide specific details about resource development in this attack.
3. Delivery: The exact method used for delivering the ransomware attack is not disclosed in the available information.
4. Social Engineering: Social engineering played a pivotal role in this breach. The attackers employed vishing (voice phishing), where they impersonated an MGM employee in a call to the company’s IT help desk. This manipulation allowed them to obtain critical credentials for unauthorized access.
5. Exploitation: The attackers exploited vulnerabilities within MGM’s systems, granting them unauthorized access and control over various parts of the network, possibly including a breach of the Okta environment..
6. Persistence: Even after detection, the attackers maintained access to MGM’s infrastructure, demonstrating their persistence in maintaining control.
7. Defense Evasion: To evade detection, the attackers continued their operations on MGM’s network, operating without immediate detection or response from the company. .
8. Command & Control: The attackers claimed to have gained super administrator privileges on MGM’s Okta environment and Global Administrator permissions for the company’s Azure tenant, enabling them to communicate with and control systems within the target network.
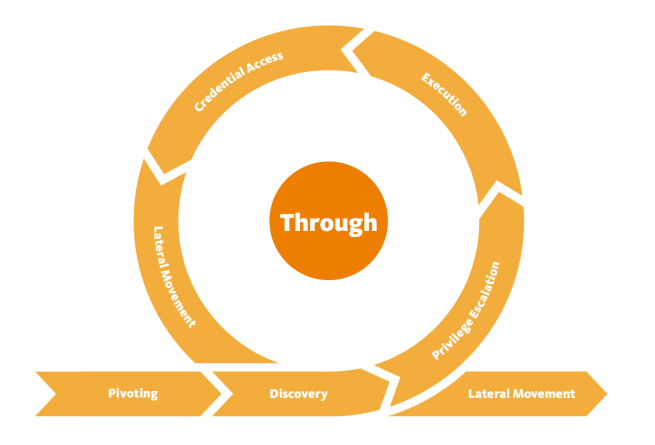
9. Pivoting: Positioned within MGM’s network, the attackers were poised to carry out additional attacks or actions not directly accessible from their initial point of entry.
10. Discovery: Engaging in reconnaissance, the attackers acquired knowledge about MGM’s systems, network environment, and user credentials, enhancing their ability to navigate and exploit the network.
11. Privilege Escalation: The attackers escalated their privileges within MGM’s systems, acquiring higher permissions for greater control over the network.
12. Execution: The attackers executed the BlackCat/ALPHV ransomware on over 100 ESXi hypervisors within MGM’s infrastructure, resulting in the encryption of a significant portion of MGM’s systems.
13. Credential Access: Various credentials were accessed and controlled by the attackers, likely including system, service, or domain credentials, facilitating their unauthorized activities.
14. Lateral Movement: The attackers moved laterally within the network, extending their reach to access and control other remote systems within MGM’s network.
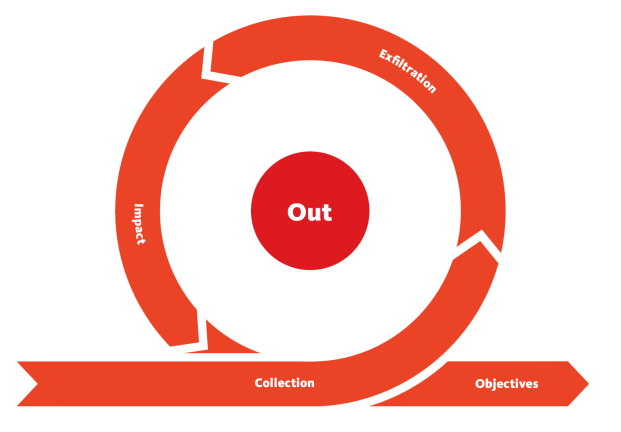
15. Collection: The attackers claimed to have exfiltrated data from MGM’s network, gathering sensitive information from the compromised systems.
16. Exfiltration: To pressure MGM Resorts, the attackers threatened to exfiltrate the stolen data unless the company agreed to pay a ransom.
17. Impact: The attack had a significant impact on MGM Resorts, disrupting its operations, causing inconvenience to guests, and potentially leading to financial losses.
18. Objectives: The attackers’ socio-technical objectives included encrypting data, exfiltrating sensitive information, and pressuring MGM Resorts into negotiating a ransom payment, highlighting the strategic goals of the attack.
It’s essential to emphasize that the MGM Resorts cyberattack is not an exhaustive case study within the UKC framework, as many details remain undisclosed. However, this analysis provides a glimpse into how the UKC can help dissect and understand complex cyber incidents.
For more information about the MGM Resorts cyberattack, you can refer to the following sources:
In the ever-evolving landscape of cybersecurity, frameworks like the Unified Kill Chain play a vital role in enhancing our understanding of cyber threats. Stay vigilant, stay informed, and keep learning.